

HIPAA Compliant eSignature: Securely Sign Patient Documents Online

As the healthcare landscape evolves, protecting sensitive patient information while streamlining administrative processes has become more critical than ever. Healthcare providers face mounting pressure to digitize operations without compromising security or compliance. This is where HIPAA compliant esignature solutions bridge the gap, offering robust protection for patient data while dramatically improving operational efficiency.
The Health Insurance Portability and Accountability Act (HIPAA) establishes stringent requirements for safeguarding protected health information (PHI). Digital signatures must meet these standards to be considered compliant, and healthcare organizations need solutions that simplify document signing while ensuring confidentiality, integrity, and availability of sensitive data. This comprehensive guide explores what makes an eSignature HIPAA compliant and how healthcare providers can leverage these tools effectively.
What Makes an eSignature HIPAA Compliant?
Understanding the distinction between standard eSignatures and HIPAA compliant esignature solutions is crucial for healthcare organizations. While regular electronic signatures might suffice for general business transactions, healthcare requires specialized tools that meet rigorous security standards.
According to the HIPAA Security Rule, covered entities must implement appropriate administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of ePHI.
Advanced Encryption
The core components of HIPAA-compliant electronic signatures include advanced encryption standards where all electronic protected health information must be encrypted during transmission and storage. This typically involves AES-256 bit encryption for data at rest and TLS 1.2 or higher for data in transit. These encryption standards ensure that even if data is intercepted, it remains unreadable to unauthorized parties.
Audit Trails
Comprehensive audit trails represent another critical component. The Security Rule requires regulated entities to implement hardware, software, and procedural mechanisms that record and examine activity in information systems containing ePHI.
These audit trails must capture detailed information, including who accessed the document, when access occurred, what actions were taken, any modifications made, and authentication methods used. This creates an immutable record that serves both compliance and legal purposes.
Multi-factor Authentication
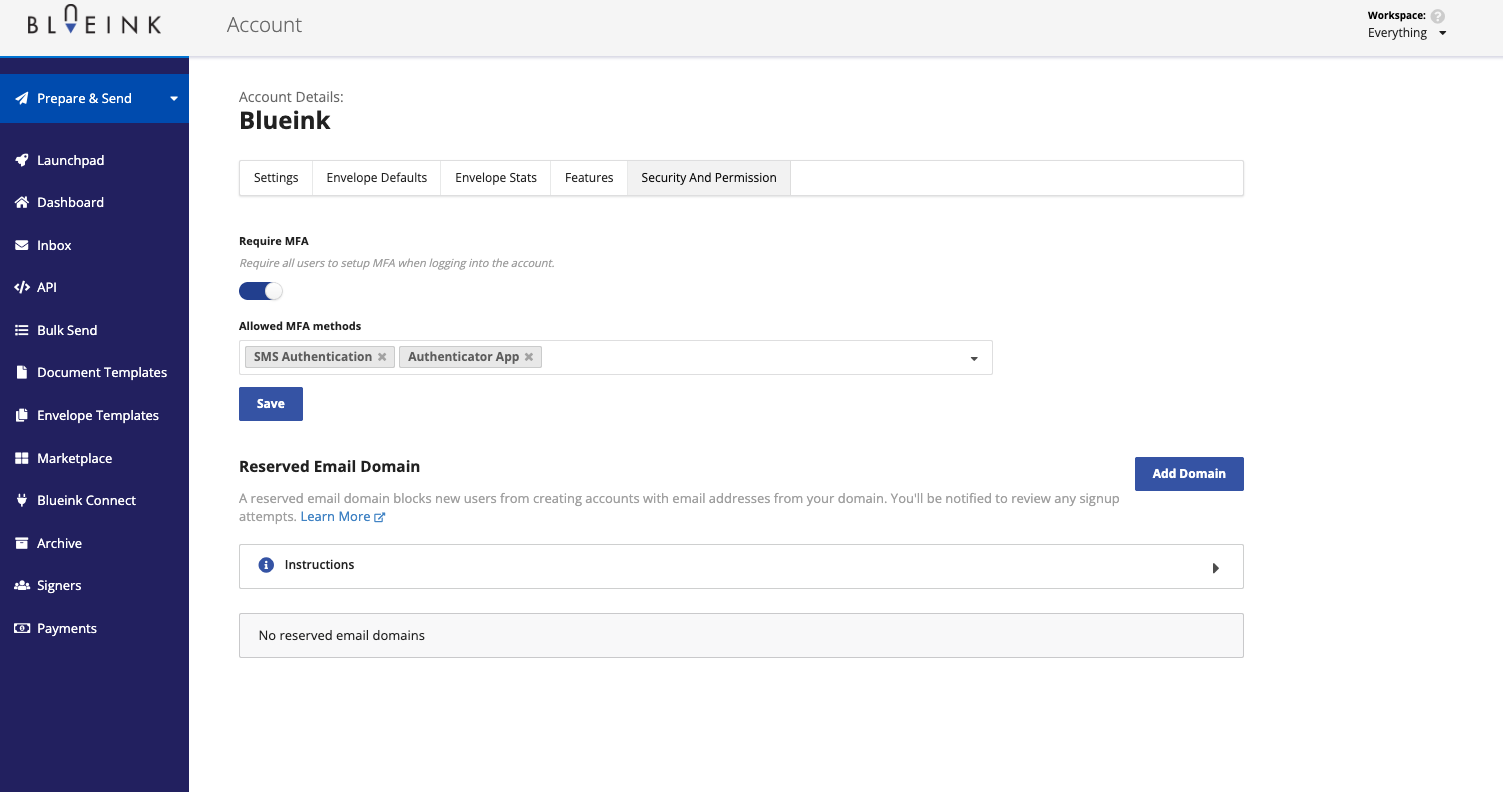
Multi-factor authentication provides strong verification measures to confirm the identity of individuals accessing ePHI. This often includes combinations of something you know, like passwords; something you have, such as mobile devices for SMS verification; and something you are, through biometric data. These layered security measures significantly reduce the risk of unauthorized access.
Business Associate Agreements
Business Associate Agreements form another essential requirement. Any third-party vendor handling ePHI must sign a BAA with the covered entity. This legal document establishes shared responsibility for protecting patient information and ensures compliance with HIPAA regulations. Without proper BAAs in place, healthcare organizations expose themselves to significant compliance risks.
The difference between standard eSignatures and HIPAA eSignature software lies in these enhanced security measures. While the ESIGN Act and UETA provide legal validity for electronic signatures, HIPAA adds layers of security requirements specifically for healthcare documentation. These additional requirements reflect the sensitive nature of medical information and the potential harm that could result from unauthorized disclosure.
Healthcare organizations must also consider the technical infrastructure supporting their esignature solution. This includes secure data centers with physical access controls, redundant systems for high availability, disaster recovery capabilities, and regular security assessments. These backend considerations are just as important as the user-facing security features.
eSignature for Healthcare: Common Use Cases
Healthcare organizations implement eSignature for healthcare across numerous processes, transforming traditional paper-based workflows into efficient digital operations. Understanding these applications helps identify opportunities for improvement and compliance enhancement.
Patient Intake
Patient intake and registration represent one of the most common applications. The traditional clipboard-and-pen approach creates bottlenecks in patient care, leading to longer wait times and potential errors in data collection. Digital intake forms allow patients to complete necessary documentation before arriving at the facility.
Blueink’s SmartLink Forms enables this seamless process, allowing patients to fill out and submit forms from any device without requiring account creation or app downloads.
Consent Management
Consent management presents another critical application area. Healthcare providers must obtain informed consent for procedures, treatments, and data sharing. Digital consent forms streamline this vital process while ensuring legal compliance. Electronic consents can reduce wait times and administrative burdens while improving the patient experience.
Telehealth Documentation
Telehealth documentation has become increasingly important as virtual care expands. With 82% of US respondents having used electronic medical records, according to a Suvoda survey, the need for secure remote signing capabilities has never been greater. Telehealth requires secure methods for obtaining signatures on consent forms, treatment plans, and follow-up instructions.
Internal Compliance and HR
Internal compliance and HR processes also benefit from digital signatures. Healthcare organizations must maintain extensive documentation for employee training, credentialing, and policy acknowledgments. Digital signatures streamline these processes while creating reliable audit trails for compliance purposes. This includes HIPAA training certifications, annual policy reviews, credential verifications, and employment agreements.
Real-world implementations demonstrate significant benefits across these use cases. Urban Health Plan achieved remarkable results with their digital transformation after implementing Blueink, including a 100% user adoption rate and 50% cost reduction after implementing digital signatures. Similarly, California Fertility Partners reported an 80% reduction in document errors and a 95% increase in patient satisfaction.
Beyond these primary applications, healthcare providers utilize esignatures in specialized areas such as research consent forms for clinical trials, prescription management documentation, care coordination agreements between providers, and financial assistance applications. Each of these use cases requires careful consideration of security and compliance requirements specific to the document type and workflow.
Security Features Required for Patient Documents
Protecting patient information demands multiple layers of security that go far beyond basic password protection. Healthcare organizations must implement comprehensive safeguards that align with HIPAA's technical safeguards requirements.
Encryption
End-to-end encryption forms the foundation of any secure eSignature for patient documents. Healthcare data must be protected both in transit and at rest. The Security Rule specifically requires covered entities to implement mechanisms to encrypt and decrypt electronic protected health information.
This encryption typically includes AES-256 bit encryption for stored data, TLS 1.2 or higher for data transmission, secure key management protocols, and regular encryption key rotation. These measures ensure that even if data is intercepted or accessed without authorization, it remains unreadable and unusable to malicious actors.
Identity Verification

Identity verification methods play a crucial role in confirming the identity of document signers and preventing fraud. Modern HIPAA compliant solutions offer multiple verification options including knowledge-based authentication where users answer personal questions, SMS PIN verification for mobile confirmation, email verification with secure links, government ID verification for high-security needs, and biometric authentication such as fingerprint or facial recognition.
The level of verification can be adjusted based on document sensitivity and organizational policies. For instance, a routine consent form might require only email verification, while surgical consent might demand multi-factor authentication combining several verification methods.
Tamper-proof Audit Trail

Tamper-evident technology ensures document integrity throughout the signing process. Digital signatures create an unalterable record of the signing event using cryptographic hash functions to generate a unique fingerprint for each document. Any modification, no matter how minor, changes this fingerprint and immediately flags the document as altered.
The audit trail must capture comprehensive information about document access and modifications. This includes tracking who accessed patient records and when, which is vital for maintaining compliance.
Access Controls
Access controls and permissions implement HIPAA's minimum necessary standard, ensuring that access to ePHI is limited to only what's needed for specific job functions. Role-based access control systems allow administrators to define user roles and permissions, restrict document access by department or function, set time-limited access for temporary staff, and monitor all access attempts.
Mobile Security
Mobile security considerations have become increasingly important as healthcare embraces mobile technology. Security must extend to all devices, maintaining the same standards across platforms. This includes secure app architecture, device authentication requirements, encrypted data transmission protocols, and remote wipe capabilities for lost or stolen devices.
Document Retention
Document retention and disposal procedures round out the security framework. Healthcare organizations must maintain signed documents for legally required periods while ensuring secure disposal when retention requirements expire. This includes implementing secure deletion protocols and maintaining documentation of disposal activities.
Why Blueink Is a HIPAA Compliant eSignature Solution
Blueink stands out as a purpose-built HIPAA compliant eSignature solution designed specifically for healthcare's unique challenges. Unlike generic eSignature platforms, Blueink addresses the complex intersection of security, compliance, and usability that healthcare organizations require.
Compliance Features

Built-in HIPAA compliance forms the foundation of Blueink's offering. The platform provides Business Associate Agreements as standard for all healthcare clients, demonstrating commitment to shared responsibility for PHI protection. Blueink ensures all documentation meets strict regulatory standards with robust compliance features.
Security Features
The advanced security architecture incorporates multiple protective layers, including military-grade encryption for all data, comprehensive audit trails tracking every interaction, multi-factor authentication options, regular security audits and penetration testing, and SOC 2 Type II compliance certification. These features work together to create a secure environment for handling sensitive healthcare documents.
Flexible authentication options allow organizations to customize security requirements based on document type and risk level. The platform offers multi-layered identity verification, including ID checks, selfies, and SMS pins.
What Makes Blueink Stand Out?
Beyond the compliance and security features, Blueink is the #1 Docusign alternative due to the following reasons:
Integrations

Seamless integration capabilities distinguish Blueink from many competitors. The platform integrates with existing healthcare systems, allowing organizations to seamlessly embed advanced eSignature functionalities into their existing workflows. This integration reduces duplicate data entry, minimizes errors, and creates efficient processes that save time for both staff and patients.
User-friendly Interface
Despite robust security measures, Blueink maintains a user-friendly experience. Patients can sign documents from any device without creating accounts or downloading apps. The SmartLink feature allows document initiation via SmartLink URLs or embedded forms, perfect for frequently used documents and high-volume workflows.
Cost-Effective Implementation
Cost-effective implementation makes Blueink particularly attractive for healthcare organizations operating under budget constraints. The platform offers premium features at approximately 50% less than traditional providers. Organizations report significant savings through reduced paper and printing costs, decreased administrative time, faster document turnaround, improved cash flow, and minimized storage requirements.
Real-world results validate these benefits across various healthcare settings. For example, Medical Resources achieved remarkable outcomes, including a 100% compliance rate and 80% cost savings, while maintaining strict security standards. These results demonstrate that organizations can achieve both compliance and cost savings simultaneously.
Implementation Best Practices and Considerations
Successfully implementing a HIPAA compliant eSignature system requires careful planning and execution. Healthcare organizations should consider several key factors to ensure smooth adoption and maximize its use.
Comprehensive Risk Assessment
Conducting a comprehensive risk assessment forms the critical first step. Before implementation, organizations must evaluate their current document workflows, identify security vulnerabilities, and assess compliance gaps. This assessment should align with HIPAA's requirement to perform accurate and thorough evaluations of potential risks to ePHI.
Standard Policies and Procedures
Developing clear policies and procedures ensures consistent application of security measures. Written policies must address who can access and sign documents electronically, authentication requirements for different document types, audit trail retention periods, incident response procedures, and regular security review processes. These policies create a framework for compliant operations and provide guidance for staff members.
Comprehensive Training
Providing comprehensive training helps ensure successful adoption. Staff education should cover technical aspects of the eSignature system, HIPAA compliance requirements, security best practices, patient communication guidelines, and troubleshooting common issues. Regular refresher training helps maintain high standards and addresses new features or requirements as they emerge.
Performance Monitoring and Optimization
Monitoring and optimizing performance allows organizations to maximize their investment. Regular monitoring helps identify usage patterns and adoption rates, security incidents or attempted breaches, workflow bottlenecks, and user feedback for improvement opportunities. This ongoing evaluation ensures the system continues to meet organizational needs while maintaining security and compliance.
Change Management Strategies
Change management strategies play a crucial role in successful implementation. Healthcare organizations should develop communication plans to inform staff and patients about the new system, create support resources for common questions, identify champions within each department, and celebrate early successes to build momentum.
Digital Transformation in the Healthcare Industry: Are You Ready?
The healthcare industry's digital transformation demands solutions that balance security, compliance, and efficiency. HIPAA compliant eSignature platforms represent a critical component of this transformation, enabling organizations to modernize operations while protecting patient information.
As healthcare continues to evolve, organizations that embrace secure digital solutions position themselves for long-term success. The right eSignature platform not only ensures regulatory compliance but also contributes to improved patient care through efficient document management.
When evaluating solutions, prioritize vendors that offer comprehensive security features meeting HIPAA standards, flexible authentication options, seamless integration capabilities, reliable customer support with proper BAAs, and a proven track record in healthcare. These criteria help ensure that the chosen solution will meet both current and future needs.
Ready to simplify patient document signing? Try Blueink's HIPAA compliant esignature solution today — secure, fast, and fully compliant.
Disclaimer
Blueink is not a law firm and does not provide legal advice. This page is for informational purposes only and should not be considered a substitute for professional legal counsel. If you have questions about the validity or enforceability of eSignatures or digital signatures, we recommend consulting with a licensed attorney. Use of Blueink’s services is subject to our Terms of Use and Privacy Policy.


Weekly Newsletter
Get the latest updates, tips, and exclusive offers. Sign up for our weekly newsletter and stay informed!
Recent post
January 21, 2026
January 13, 2026
January 10, 2026
As the healthcare landscape evolves, protecting sensitive patient information while streamlining administrative processes has become more critical than ever. Healthcare providers face mounting pressure to digitize operations without compromising security or compliance. This is where HIPAA compliant esignature solutions bridge the gap, offering robust protection for patient data while dramatically improving operational efficiency.
The Health Insurance Portability and Accountability Act (HIPAA) establishes stringent requirements for safeguarding protected health information (PHI). Digital signatures must meet these standards to be considered compliant, and healthcare organizations need solutions that simplify document signing while ensuring confidentiality, integrity, and availability of sensitive data. This comprehensive guide explores what makes an eSignature HIPAA compliant and how healthcare providers can leverage these tools effectively.
What Makes an eSignature HIPAA Compliant?
Understanding the distinction between standard eSignatures and HIPAA compliant esignature solutions is crucial for healthcare organizations. While regular electronic signatures might suffice for general business transactions, healthcare requires specialized tools that meet rigorous security standards.
According to the HIPAA Security Rule, covered entities must implement appropriate administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of ePHI.
Advanced Encryption
The core components of HIPAA-compliant electronic signatures include advanced encryption standards where all electronic protected health information must be encrypted during transmission and storage. This typically involves AES-256 bit encryption for data at rest and TLS 1.2 or higher for data in transit. These encryption standards ensure that even if data is intercepted, it remains unreadable to unauthorized parties.
Audit Trails
Comprehensive audit trails represent another critical component. The Security Rule requires regulated entities to implement hardware, software, and procedural mechanisms that record and examine activity in information systems containing ePHI.
These audit trails must capture detailed information, including who accessed the document, when access occurred, what actions were taken, any modifications made, and authentication methods used. This creates an immutable record that serves both compliance and legal purposes.
Multi-factor Authentication

Multi-factor authentication provides strong verification measures to confirm the identity of individuals accessing ePHI. This often includes combinations of something you know, like passwords; something you have, such as mobile devices for SMS verification; and something you are, through biometric data. These layered security measures significantly reduce the risk of unauthorized access.
Business Associate Agreements
Business Associate Agreements form another essential requirement. Any third-party vendor handling ePHI must sign a BAA with the covered entity. This legal document establishes shared responsibility for protecting patient information and ensures compliance with HIPAA regulations. Without proper BAAs in place, healthcare organizations expose themselves to significant compliance risks.
The difference between standard eSignatures and HIPAA eSignature software lies in these enhanced security measures. While the ESIGN Act and UETA provide legal validity for electronic signatures, HIPAA adds layers of security requirements specifically for healthcare documentation. These additional requirements reflect the sensitive nature of medical information and the potential harm that could result from unauthorized disclosure.
Healthcare organizations must also consider the technical infrastructure supporting their esignature solution. This includes secure data centers with physical access controls, redundant systems for high availability, disaster recovery capabilities, and regular security assessments. These backend considerations are just as important as the user-facing security features.
eSignature for Healthcare: Common Use Cases
Healthcare organizations implement eSignature for healthcare across numerous processes, transforming traditional paper-based workflows into efficient digital operations. Understanding these applications helps identify opportunities for improvement and compliance enhancement.
Patient Intake
Patient intake and registration represent one of the most common applications. The traditional clipboard-and-pen approach creates bottlenecks in patient care, leading to longer wait times and potential errors in data collection. Digital intake forms allow patients to complete necessary documentation before arriving at the facility.
Blueink’s SmartLink Forms enables this seamless process, allowing patients to fill out and submit forms from any device without requiring account creation or app downloads.
Consent Management
Consent management presents another critical application area. Healthcare providers must obtain informed consent for procedures, treatments, and data sharing. Digital consent forms streamline this vital process while ensuring legal compliance. Electronic consents can reduce wait times and administrative burdens while improving the patient experience.
Telehealth Documentation
Telehealth documentation has become increasingly important as virtual care expands. With 82% of US respondents having used electronic medical records, according to a Suvoda survey, the need for secure remote signing capabilities has never been greater. Telehealth requires secure methods for obtaining signatures on consent forms, treatment plans, and follow-up instructions.
Internal Compliance and HR
Internal compliance and HR processes also benefit from digital signatures. Healthcare organizations must maintain extensive documentation for employee training, credentialing, and policy acknowledgments. Digital signatures streamline these processes while creating reliable audit trails for compliance purposes. This includes HIPAA training certifications, annual policy reviews, credential verifications, and employment agreements.
Real-world implementations demonstrate significant benefits across these use cases. Urban Health Plan achieved remarkable results with their digital transformation after implementing Blueink, including a 100% user adoption rate and 50% cost reduction after implementing digital signatures. Similarly, California Fertility Partners reported an 80% reduction in document errors and a 95% increase in patient satisfaction.
Beyond these primary applications, healthcare providers utilize esignatures in specialized areas such as research consent forms for clinical trials, prescription management documentation, care coordination agreements between providers, and financial assistance applications. Each of these use cases requires careful consideration of security and compliance requirements specific to the document type and workflow.
Security Features Required for Patient Documents
Protecting patient information demands multiple layers of security that go far beyond basic password protection. Healthcare organizations must implement comprehensive safeguards that align with HIPAA's technical safeguards requirements.
Encryption
End-to-end encryption forms the foundation of any secure eSignature for patient documents. Healthcare data must be protected both in transit and at rest. The Security Rule specifically requires covered entities to implement mechanisms to encrypt and decrypt electronic protected health information.
This encryption typically includes AES-256 bit encryption for stored data, TLS 1.2 or higher for data transmission, secure key management protocols, and regular encryption key rotation. These measures ensure that even if data is intercepted or accessed without authorization, it remains unreadable and unusable to malicious actors.
Identity Verification

Identity verification methods play a crucial role in confirming the identity of document signers and preventing fraud. Modern HIPAA compliant solutions offer multiple verification options including knowledge-based authentication where users answer personal questions, SMS PIN verification for mobile confirmation, email verification with secure links, government ID verification for high-security needs, and biometric authentication such as fingerprint or facial recognition.
The level of verification can be adjusted based on document sensitivity and organizational policies. For instance, a routine consent form might require only email verification, while surgical consent might demand multi-factor authentication combining several verification methods.
Tamper-proof Audit Trail

Tamper-evident technology ensures document integrity throughout the signing process. Digital signatures create an unalterable record of the signing event using cryptographic hash functions to generate a unique fingerprint for each document. Any modification, no matter how minor, changes this fingerprint and immediately flags the document as altered.
The audit trail must capture comprehensive information about document access and modifications. This includes tracking who accessed patient records and when, which is vital for maintaining compliance.
Access Controls
Access controls and permissions implement HIPAA's minimum necessary standard, ensuring that access to ePHI is limited to only what's needed for specific job functions. Role-based access control systems allow administrators to define user roles and permissions, restrict document access by department or function, set time-limited access for temporary staff, and monitor all access attempts.
Mobile Security
Mobile security considerations have become increasingly important as healthcare embraces mobile technology. Security must extend to all devices, maintaining the same standards across platforms. This includes secure app architecture, device authentication requirements, encrypted data transmission protocols, and remote wipe capabilities for lost or stolen devices.
Document Retention
Document retention and disposal procedures round out the security framework. Healthcare organizations must maintain signed documents for legally required periods while ensuring secure disposal when retention requirements expire. This includes implementing secure deletion protocols and maintaining documentation of disposal activities.
Why Blueink Is a HIPAA Compliant eSignature Solution
Blueink stands out as a purpose-built HIPAA compliant eSignature solution designed specifically for healthcare's unique challenges. Unlike generic eSignature platforms, Blueink addresses the complex intersection of security, compliance, and usability that healthcare organizations require.
Compliance Features

Built-in HIPAA compliance forms the foundation of Blueink's offering. The platform provides Business Associate Agreements as standard for all healthcare clients, demonstrating commitment to shared responsibility for PHI protection. Blueink ensures all documentation meets strict regulatory standards with robust compliance features.
Security Features
The advanced security architecture incorporates multiple protective layers, including military-grade encryption for all data, comprehensive audit trails tracking every interaction, multi-factor authentication options, regular security audits and penetration testing, and SOC 2 Type II compliance certification. These features work together to create a secure environment for handling sensitive healthcare documents.
Flexible authentication options allow organizations to customize security requirements based on document type and risk level. The platform offers multi-layered identity verification, including ID checks, selfies, and SMS pins.
What Makes Blueink Stand Out?
Beyond the compliance and security features, Blueink is the #1 Docusign alternative due to the following reasons:
Integrations

Seamless integration capabilities distinguish Blueink from many competitors. The platform integrates with existing healthcare systems, allowing organizations to seamlessly embed advanced eSignature functionalities into their existing workflows. This integration reduces duplicate data entry, minimizes errors, and creates efficient processes that save time for both staff and patients.
User-friendly Interface
Despite robust security measures, Blueink maintains a user-friendly experience. Patients can sign documents from any device without creating accounts or downloading apps. The SmartLink feature allows document initiation via SmartLink URLs or embedded forms, perfect for frequently used documents and high-volume workflows.
Cost-Effective Implementation
Cost-effective implementation makes Blueink particularly attractive for healthcare organizations operating under budget constraints. The platform offers premium features at approximately 50% less than traditional providers. Organizations report significant savings through reduced paper and printing costs, decreased administrative time, faster document turnaround, improved cash flow, and minimized storage requirements.
Real-world results validate these benefits across various healthcare settings. For example, Medical Resources achieved remarkable outcomes, including a 100% compliance rate and 80% cost savings, while maintaining strict security standards. These results demonstrate that organizations can achieve both compliance and cost savings simultaneously.
Implementation Best Practices and Considerations
Successfully implementing a HIPAA compliant eSignature system requires careful planning and execution. Healthcare organizations should consider several key factors to ensure smooth adoption and maximize its use.
Comprehensive Risk Assessment
Conducting a comprehensive risk assessment forms the critical first step. Before implementation, organizations must evaluate their current document workflows, identify security vulnerabilities, and assess compliance gaps. This assessment should align with HIPAA's requirement to perform accurate and thorough evaluations of potential risks to ePHI.
Standard Policies and Procedures
Developing clear policies and procedures ensures consistent application of security measures. Written policies must address who can access and sign documents electronically, authentication requirements for different document types, audit trail retention periods, incident response procedures, and regular security review processes. These policies create a framework for compliant operations and provide guidance for staff members.
Comprehensive Training
Providing comprehensive training helps ensure successful adoption. Staff education should cover technical aspects of the eSignature system, HIPAA compliance requirements, security best practices, patient communication guidelines, and troubleshooting common issues. Regular refresher training helps maintain high standards and addresses new features or requirements as they emerge.
Performance Monitoring and Optimization
Monitoring and optimizing performance allows organizations to maximize their investment. Regular monitoring helps identify usage patterns and adoption rates, security incidents or attempted breaches, workflow bottlenecks, and user feedback for improvement opportunities. This ongoing evaluation ensures the system continues to meet organizational needs while maintaining security and compliance.
Change Management Strategies
Change management strategies play a crucial role in successful implementation. Healthcare organizations should develop communication plans to inform staff and patients about the new system, create support resources for common questions, identify champions within each department, and celebrate early successes to build momentum.
Digital Transformation in the Healthcare Industry: Are You Ready?
The healthcare industry's digital transformation demands solutions that balance security, compliance, and efficiency. HIPAA compliant eSignature platforms represent a critical component of this transformation, enabling organizations to modernize operations while protecting patient information.
As healthcare continues to evolve, organizations that embrace secure digital solutions position themselves for long-term success. The right eSignature platform not only ensures regulatory compliance but also contributes to improved patient care through efficient document management.
When evaluating solutions, prioritize vendors that offer comprehensive security features meeting HIPAA standards, flexible authentication options, seamless integration capabilities, reliable customer support with proper BAAs, and a proven track record in healthcare. These criteria help ensure that the chosen solution will meet both current and future needs.
Ready to simplify patient document signing? Try Blueink's HIPAA compliant esignature solution today — secure, fast, and fully compliant.


